—————
Free Secure Email – Transcom Sigma
Boost Inflight Internet
Transcom Hosting
Transcom Premium Domains
News
Brute-Forcing a Fingerprint Reader
It’s neither hard nor expensive:
Unlike password authentication, which requires a direct match between what is inputted and what’s stored in a database, fingerprint authentication determines a match using a reference threshold. As a result, a successful fingerprint brute-force attack requires only that an inputted image provides an acceptable approximation of an image in the fingerprint database. BrutePrint manipulates the false acceptance rate (FAR) to increase the threshold so fewer approximate images are accepted.
BrutePrint acts as an adversary in the middle between the fingerprint sensor and the trusted execution environment and exploits vulnerabilities that allow for unlimited guesses.
In a BrutePrint attack, the adversary removes the back cover of the device and attaches the $15 circuit board that has the fingerprint database loaded in the flash storage. The adversary then must convert the database into a fingerprint dictionary that’s formatted to work with the specific sensor used by the targeted phone. The process uses a neural-style transfer when converting the database into the usable dictionary. This process increases the chances of a match.
With the fingerprint dictionary in place, the adversary device is now in a position to input each entry into the targeted phone. Normally, a protection known as attempt limiting effectively locks a phone after a set number of failed login attempts are reached. BrutePrint can fully bypass this limit in the eight tested Android models, meaning the adversary device can try an infinite number of guesses. (On the two iPhones, the attack can expand the number of guesses to 15, three times higher than the five permitted.)
The bypasses result from exploiting what the researchers said are two zero-day vulnerabilities in the smartphone fingerprint authentication framework of virtually all smartphones. The vulnerabilities—one known as CAMF (cancel-after-match fail) and the other MAL (match-after-lock)—result from logic bugs in the authentication framework. CAMF exploits invalidate the checksum of transmitted fingerprint data, and MAL exploits infer matching results through side-channel attacks.
Depending on the model, the attack takes between 40 minutes and 14 hours.
Also:
The ability of BrutePrint to successfully hijack fingerprints stored on Android devices but not iPhones is the result of one simple design difference: iOS encrypts the data, and Android does not.
—————
Free Secure Email – Transcom Sigma
Boost Inflight Internet
Transcom Hosting
Transcom Premium Domains
Discord Admins Hacked by Malicious Bookmarks
A number of Discord communities focused on cryptocurrency have been hacked this past month after their administrators were tricked into running malicious Javascript code disguised as a Web browser bookmark.
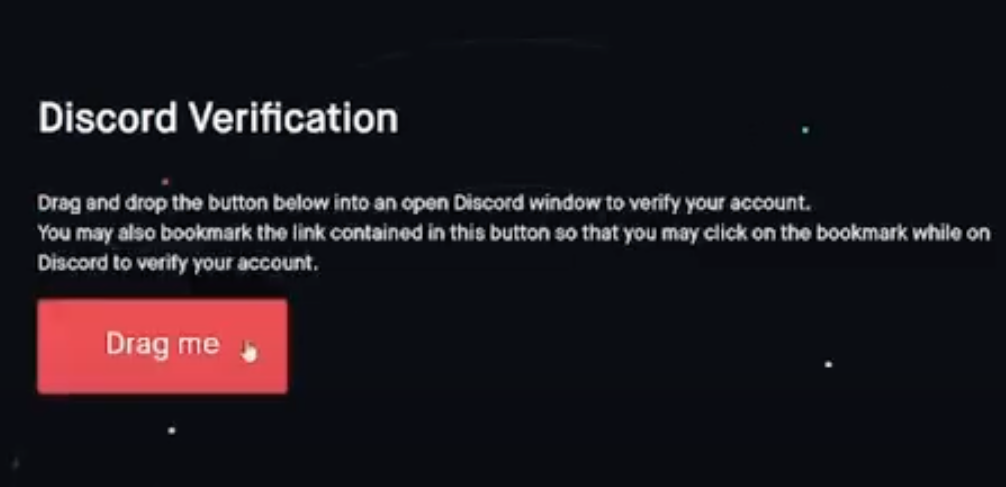
This attack involves malicious Javascript that is added to one’s browser by dragging a component from a web page to one’s browser bookmarks.
According to interviews with victims, several of the attacks began with an interview request from someone posing as a reporter for a crypto-focused news outlet online. Those who take the bait are sent a link to a Discord server that appears to be the official Discord of the crypto news site, where they are asked to complete a verification step to validate their identity.
As shown in this Youtube video, the verification process involves dragging a button from the phony crypto news Discord server to the bookmarks bar in one’s Web browser. From there, the visitor is instructed to go back to discord.com and then click the new bookmark to complete the verification process.
However, the bookmark is actually a clever snippet of Javascript that quietly grabs the user’s Discord token and sends it to the scammer’s website. The attacker then loads the stolen token into their own browser session and (usually late at night after the admins are asleep) posts an announcement in the targeted Discord about an exclusive “airdrop,” “NFT mint event” or some other potential money making opportunity for the Discord members.
The unsuspecting Discord members click the link provided by the compromised administrator account, and are asked to connect their crypto wallet to the scammer’s site, where it asks for unlimited spend approvals on their tokens, and subsequently drains the balance of any valuable accounts.
Meanwhile, anyone in the compromised Discord channel who notices the scam and replies is banned, and their messages are deleted by the compromised admin account.
Nicholas Scavuzzo is an associate at Ocean Protocol, which describes itself as an “open-source protocol that aims to allow businesses and individuals to exchange and monetize data and data-based services.” On May 22, an administrator for Ocean Protocol’s Discord server clicked a link in a direct message from a community member that prompted them to prove their identity by dragging a link to their bookmarks.
Scavuzzo, who is based in Maine, said the attackers waited until around midnight in his timezone time before using the administrator’s account to send out an unauthorized message about a new Ocean airdrop.
Scavuzzo said the administrator’s account was hijacked even though she had multi-factor authentication turned on.
“A CAPTCHA bot that allows Discord cookies to be accessed by the person hosting the CAPTCHA,” was how Scavuzzo described the attack. “I’ve seen all kinds of crypto scams, but I’ve never seen one like this.”
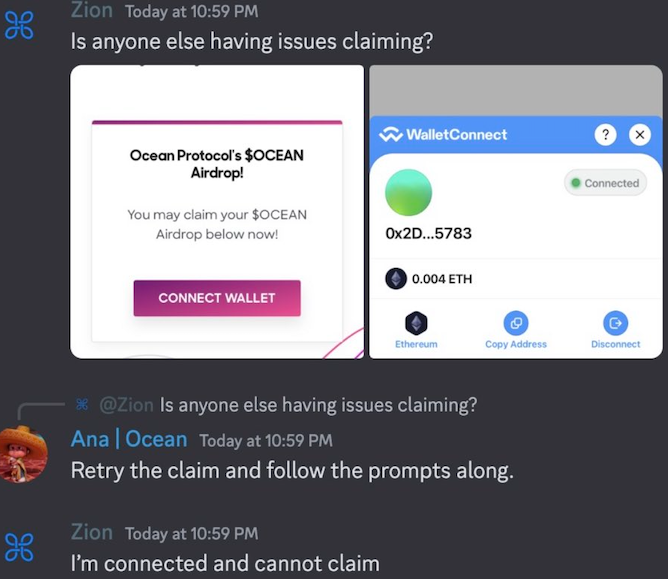
In this conversation, “Ana | Ocean” is a compromised Discord server administrator account promoting a phony airdrop.
Importantly, the stolen token only works for the attackers as long as its rightful owner doesn’t log out and back in, or else change their credentials.
Assuming the administrator can log in, that is. In Ocean’s case, one of the first things the intruders did once they swiped the administrator’s token was change the server’s access controls and remove all core Ocean team members from the server.
Fortunately for Ocean, Scavuzzo was able to reach the operator of the server that hosts the Discord channel, and have the channel’s settings reverted back to normal.
“Thankfully, we are a globally distributed team, so we have people awake at all hours,” Scavuzzo said, noting that Ocean is not aware of any Discord community members who fell for the phony airdrop offer, which was live for about 30 minutes. “This could have been a lot worse.”
On May 26, Aura Network reported on Twitter that its Discord server was compromised in a phishing attack that resulted in the deletion of Discord channels and the dissemination of fake Aura Network Airdrop Campaign links.
On May 27, Nahmii — a cryptocurrency technology based on the Ethereum blockchain — warned on Twitter that one of its community moderators on Discord was compromised and posting fake airdrop details.
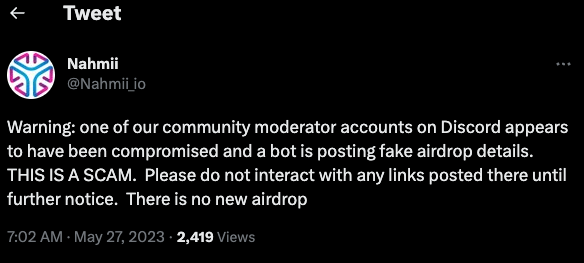
On May 9, MetrixCoin reported that its Discord server was hacked, with fake airdrop details pushed to all users.
KrebsOnSecurity recently heard from a trusted source in the cybersecurity industry who dealt firsthand with one of these attacks and asked to remain anonymous.
“I do pro bono Discord security work for a few Discords, and I was approached by one of these fake journalists,” the source said. “I played along and got the link to their Discord, where they were pretending to be journalists from the Cryptonews website using several accounts.”
The source took note of all the Discord IDs of the admins of the fake Cryptonews Discord, so that he could ensure they were blocked from the Discords he helps to secure.
“Since I’ve been doing this for a while now, I’ve built up a substantial database of Discord users and messages, so often I can see these scammers’ history on Discord,” the source said.
In this case, he noticed a user with the “CEO” role in the fake Cryptonews Discord had been seen previously under another username — “Levatax.” Searching on that Discord ID and username revealed a young Turkish coder named Berk Yilmaz whose Github page linked to the very same Discord ID as the scammer CEO.
Reached via instant message on Telegram, Levatax said he’s had no involvement in such schemes, and that he hasn’t been on Discord since his Microsoft Outlook account was hacked months ago.
“The interesting thing [is] that I didn’t use Discord since few months or even social media because of the political status of Turkey,” Levatax explained, referring to the recent election in his country. “The only thing I confirm is losing my Outlook account which connected to my Discord, and I’m already in touch with Microsoft to recover it.”
The verification method used in the above scam involves a type of bookmark called a “bookmarklet” that stores Javascript code as a clickable link in the bookmarks bar at the top of one’s browser.
While bookmarklets can be useful and harmless, malicious Javascript that is executed in the browser by the user is especially dangerous. So please avoid adding (or dragging) any bookmarks or bookmarklets to your browser unless it was your idea in the first place.
—————
Free Secure Email – Transcom Sigma
Boost Inflight Internet
Transcom Hosting
Transcom Premium Domains
New Mirai Variant Campaigns are Targeting IoT Devices
—————
Free Secure Email – Transcom Sigma
Boost Inflight Internet
Transcom Hosting
Transcom Premium Domains
Anyone Can Try ChatGPT for Free—Don’t Fall for Sketchy Apps That Charge You

Anyone can try ChatGPT for free. Yet that hasn’t stopped scammers from trying to cash in on it.
A rash of sketchy apps have cropped up in Apple’s App Store and Google Play. They pose as Chat GPT apps and try to fleece smartphone owners with phony subscriptions.
Yet you can spot them quickly when you know what to look for.
What is ChatGPT, and what are people doing with it?
ChatGPT is an AI-driven chatbot service created by OpenAI. It lets you have uncannily human conversations with an AI that’s been programmed and fed with information over several generations of development. Provide it with an instruction or ask it a question, and the AI provides a detailed response.
Unsurprisingly, it has millions of people clamoring to use it. All it takes is a single prompt, and the prompts range far and wide.
People ask ChatGPT to help them write cover letters for job interviews, make travel recommendations, and explain complex scientific topics in plain language. One person highlighted how they used ChatGPT to run a tabletop game of Dungeons & Dragons for them. (If you’ve ever played, you know that’s a complex task that calls for a fair share of cleverness to keep the game entertaining.)
That’s just a handful of examples. As for myself, I’ve been using ChatGPT in the kitchen. My family and I have been digging into all kinds of new recipes thanks to its AI.
Sketchy ChatGPT apps in the App Store and Google Play
So, where do the scammers come in?
Scammers, have recently started posting copycat apps that look like they are powered by ChatGPT but aren’t. What’s more, they charge people a fee to use them—a prime example of fleeceware. OpenAI, the makers of ChatGPT, have just officially launched their iOS app for U.S. iPhone users and can be downloaded from the Apple App Store here. The official Android version is still yet to be released.
Fleeceware mimics a pre-existing service that’s free or low-cost and then charges an excessive fee to use it. Basically, it’s a copycat. An expensive one at that.
Fleeceware scammers often lure in their victims with “a free trial” that quickly converts into a subscription. However, with fleeceware, the terms of the subscription are steep. They might bill the user weekly, and at rates much higher than the going rate.
The result is that the fleeceware app might cost the victim a few bucks before they can cancel it. Worse yet, the victim might forget about the app entirely and run up hundreds of dollars before they realize what’s happening. Again, all for a simple app that’s free or practically free elsewhere.
What makes fleeceware so tricky to spot is that it can look legit at first glance. Plenty of smartphone apps offer subscriptions and other in-app purchases. In effect, fleeceware hides in plain sight among the thousands of other legitimate apps in the hopes you’ll download it.
With that, any app that charges a fee to use ChatGPT is fleeceware. ChatGPT offers basic functionality that anyone can use for free.
There is one case where you might pay a fee to use ChatGPT. It has its own subscription-level offering, ChatGPT Plus. With a subscription, ChatGPT responds more quickly to prompts and offers access during peak hours when free users might be shut out. That’s the one legitimate case where you might pay to use it.
In all, more and more people want to take ChatGPT for a spin. However, they might not realize it’s free. Scammers bank on that, and so we’ve seen a glut of phony ChatGPT apps that aim to install fleeceware onto people’s phones.
How do you keep fleeceware and other bad apps off your phone?
Read the fine print.
Read the description of the app and see what the developer is really offering. If the app charges you to use ChatGPT, it’s fleeceware. Anyone can use ChatGPT for free by setting up an account at its official website, https://chat.openai.com.
Look at the reviews.
Reviews can tell you quite a bit about an app. They can also tell you the company that created it handles customer feedback.
In the case of fleeceware, you’ll likely see reviews that complain about sketchy payment terms. They might mention three-day trials that automatically convert to pricey monthly or weekly subscriptions. Moreover, they might describe how payment terms have changed and become more costly as a result.
In the case of legitimate apps, billing issues can arise from time to time, so see how the company handles complaints. Companies in good standing will typically provide links to customer service where people can resolve any issues they have. Company responses that are vague, or a lack of responses at all, should raise a red flag.
Be skeptical about overwhelmingly positive reviews.
Scammers are smart. They’ll count on you to look at an overall good review of 4/5 stars or more and think that’s good enough. They know this, so they’ll pack their app landing page with dozens and dozens of phony and fawning reviews to make the app look legitimate. This tactic serves another purpose: it hides the true reviews written by actual users, which might be negative because the app is a scam.
Filter the app’s reviews for the one-star reviews and see what concerns people have. Do they mention overly aggressive billing practices, like the wickedly high prices and weekly billing cycles mentioned above? That might be a sign of fleeceware. Again, see if the app developer responded to the concerns and note the quality of the response. A legitimate company will honestly want to help a frustrated user and provide clear next steps to resolve the issue.
Steer clear of third-party app stores.
Google Play does its part to keep its virtual shelves free of malware-laden apps with a thorough submission process, as reported by Google. It further keeps things safer through its App Defense Alliance that shares intelligence across a network of partners, of which we’re a proud member. Further, users also have the option of running Play Protect to check apps for safety before they’re downloaded. Apple’s App Store has its own rigorous submission process for submitting apps. Likewise, Apple deletes hundreds of thousands of malicious apps from its store each year.
Third-party app stores might not have protections like these in place. Moreover, some of them might be fronts for illegal activity. Organized cybercrime organizations deliberately populate their third-party stores with apps that steal funds or personal information. Stick with the official app stores for the most complete protection possible.
Cancel unwanted subscriptions from your phone.
Many fleeceware apps deliberately make it tough to cancel them. You’ll often see complaints about that in reviews, “I don’t see where I can cancel my subscription!” Deleting the app from your phone is not enough. Your subscription will remain active unless you cancel your payment method.
Luckily, your phone makes it easy to cancel subscriptions right from your settings menu. Canceling makes sure your credit or debit card won’t get charged when the next billing cycle comes up.
- On iPhones and iOS devices, learn how to cancel App Store subscriptions here.
- Android users can learn how to cancel Google Play subscriptions here.
Be wary. Many fleeceware apps have aggressive billing cycles. Sometimes weekly.
The safest and best way to enjoy ChatGPT: Go directly to the source.
ChatGPT is free. Anyone can use it by setting up a free account with OpenAI at https://chat.openai.com. Smartphone apps that charge you to use it are a scam.
How to download the official ChatGPT app
You can download the official app, currently on iOS from the App Store
The post Anyone Can Try ChatGPT for Free—Don’t Fall for Sketchy Apps That Charge You appeared first on McAfee Blog.
—————
Free Secure Email – Transcom Sigma
Boost Inflight Internet
Transcom Hosting
Transcom Premium Domains
Three Reasons You Need a VPN

You know what a VPN is, but the question remains—why do you need a VPN?
There’s one good reason. Your privacy. Because it’s a commodity on today’s internet.
For starters, you have advertisers and internet service providers (ISPs) that want to know what you’re doing, when you’re doing it, where you’re doing it, and even for how long you’re doing it. They gather and use this information to create targeted ad profiles. And sometimes, they sell that information to third parties.
Next, there are the hackers and identity thieves out there. They take an even greater interest in what you’re doing online—like your shopping, banking, and finances. Even your insurance and medical matters. Primarily they want that information so they can turn a buck by hijacking your accounts or impersonating you to get medical care. In more extreme cases, they might use stolen information to impersonate you in other ways. That might include opening entirely new lines of credit or getting a driver’s license in your name.
A VPN can prevent this kind of snooping from happening.
VPNs and privacy—blocking ads and data collection
As for data collection and ads, that activity should come as no surprise. Particularly for anyone who’s seen uncannily targeted ads follow them around on the internet. Search for “summer cargo pants” one time and suddenly the sites you visit are full of ads for pants, pants, and more pants.
Aside from gathering your online activity for advertising purposes, ISPs might also sell the data they gather to third parties. They can gather that data while you’re on your home network, and they might gather it while you’re using public Wi-Fi. (Some ISPs provide free Wi-Fi in public places that allows them to collect data from people who aren’t their regular customers.)
This practice varies by region and the data privacy laws that are in place in each one.
For example, the European Union has strict data privacy laws that prevent this type of sale. (Thanks to the enactment of the GDPR, General Data Protection Regulation.) However, there are few such protections in the U.S. There, an ISP can sell the browsing history of an internet user to a third party—provided the data has been anonymized.
“Anonymized” is a key term here. It refers to the process of stripping away personal identifiers that connect a person to a set of stored data. It might also include adding “noise” to the data, which obscures personal identifiers. For example, that might remove an exact birthdate and replace it with a broad range of dates. So, “March 31, 1957” becomes “January – June 1957.”
At issue is that this anonymized data can get de-anonymized rather easily.
Researchers in 2019 found that “99.98% of Americans would be correctly re-identified in any dataset using 15 demographic attributes.” And when you consider how much data is collected about you, 15 attributes are only drops in the ocean.
Marketing and analytics companies collect hundreds and hundreds of data points on people and their households. That might include information about their mortgage, if they are allergy sufferers, whether they own cats or dogs, where they do most of their grocery shopping, and more—in addition to other information like their age and address.
What happens when that information gets breached, or published accidentally, as it did when 123 million records of U.S. households were made public back in 2017? It gives bad actors plenty of data that can potentially harm others.
Internet browsing activity doesn’t account for all the data points that these companies collect. However, the thought of your ISP tracking your time online and selling it to others might leave you feeling uncomfortable. Whether that data gets anonymized or not.
VPNs, privacy, and identity theft
The other threat to your privacy online comes from bad actors—like hackers and identity thieves. By targeting insecure networks, lurking on unsecured public Wi-Fi, or setting up phony public Wi-Fi hotspots themselves, they’ll snoop on the people using it.
On insecure networks, bad actors can watch as you log into your bank account, read your email, and see what you’re doing on the internet in general. They can steal any passwords and logins you’re using along the way, giving them access to those accounts.
In truth, this kind of snooping is more than a threat to your privacy. It enters the realm of identity theft, making the risk to your data and personal information that much greater.
Three reasons to use a VPN
With your privacy and personal identity in mind, here are three specific examples that make the case for using a VPN:
1. You value your privacy.
As outlined above, the internet has increasingly become less private. Advertisers and ISPs will track you when and where they can. When you use a VPN, you can hide several things from your ISP, like the websites and apps you use, the time spent on them, your search history, and downloads. As for websites and apps, a VPN can hide your IP address and your location, all of which can thwart ad tracking on those sites and apps.
2. You work remotely.
Many larger businesses and organizations offer (and sometimes require) a VPN for their employees who work outside the office. Smaller businesses use them less so, which makes them subject to attacks like data breaches. According to FBI reports, the average cost of a data breach for a business in 2022 was well over $150,000. Moreover, cybercriminals increasingly wage these attacks against businesses with revenues of $500,000 or less, which makes the thought of a six-figure loss even more devastating.
A VPN encrypts and protects company data in transit, whether you’re connecting from home, the airport, or anywhere outside the office. Using one protects you and the business or organization you work for.
3. You want extra protection while you bank, shop, or handle any sensitive matters online.
A strong VPN service like ours uses bank-grade encryption to keep your data and information secure. With a VPN, a snoop bad actor would only see garbled content thanks to your VPN’s encryption functionality.
Another popular reason for a VPN—streaming shows and content
If you’re traveling, you can access the sites and services you typically use at home. For example, some video streaming services aren’t available in foreign locations. By using a VPN, you can still access content by connecting through the proxy servers that VPNs use. These are servers in other locations that can make requests on your behalf. So, even if you are out of the country, you can connect to a proxy server in the U.S. and access your services as usual.
Where can I get a VPN?
If you have online protection with us, like our McAfee+ plans, you have a VPN ready to go. If not, McAfee+ offers a great way to get one.
It’s completely private and independently audited to ensure your sensitive info stays secure. We don’t log or track what you do online, so your online activity remains private.
By design, we made it simple to use. You can set it to automatically turn on if you’re on an unprotected network. Or you can also choose to keep it on all the time for an even safer online experience. With nearly 50 server locations worldwide, you can get a fast and stable VPN connection wherever you go.
And because it comes with our online protection software, you get other identity, privacy, and device security features that can keep you even safer online.
Bottom line, a VPN makes you more private and secure.
And that kind of protection is called for nowadays. Ad trackers, data collectors, hackers, and thieves—they all want to know what you’re doing online. And with a VPN, you can keep all that to yourself, making your time online more private and secure than before.
The post Three Reasons You Need a VPN appeared first on McAfee Blog.
—————
Free Secure Email – Transcom Sigma
Boost Inflight Internet
Transcom Hosting
Transcom Premium Domains
New Russian-Linked Malware Poses “Immediate Threat” to Energy Grids
—————
Free Secure Email – Transcom Sigma
Boost Inflight Internet
Transcom Hosting
Transcom Premium Domains
Romania’s Safetech Leans into UK Cybersecurity Market
—————
Free Secure Email – Transcom Sigma
Boost Inflight Internet
Transcom Hosting
Transcom Premium Domains
Friday Squid Blogging: Online Cephalopod Course
Atlas Obscura has a five-part online course on cephalopods, taught by squid biologist Dr. Sarah McAnulty.
As usual, you can also use this squid post to talk about the security stories in the news that I haven’t covered.
Read my blog posting guidelines here.
—————
Free Secure Email – Transcom Sigma
Boost Inflight Internet
Transcom Hosting
Transcom Premium Domains
Expeditionary Cyberspace Operations
Cyberspace operations now officially has a physical dimension, meaning that the United States has official military doctrine about cyberattacks that also involve an actual human gaining physical access to a piece of computing infrastructure.
A revised version of Joint Publication 3-12 Cyberspace Operations—published in December 2022 and while unclassified, is only available to those with DoD common access cards, according to a Joint Staff spokesperson—officially provides a definition for “expeditionary cyberspace operations,” which are “[c]yberspace operations that require the deployment of cyberspace forces within the physical domains.”
[…]
“Developing access to targets in or through cyberspace follows a process that can often take significant time. In some cases, remote access is not possible or preferable, and close proximity may be required, using expeditionary [cyber operations],” the joint publication states. “Such operations are key to addressing the challenge of closed networks and other systems that are virtually isolated. Expeditionary CO are often more regionally and tactically focused and can include units of the CMF or special operations forces … If direct access to the target is unavailable or undesired, sometimes a similar or partial effect can be created by indirect access using a related target that has higher-order effects on the desired target.”
[…]
“Allowing them to support [combatant commands] in this way permits faster adaptation to rapidly changing needs and allows threats that initially manifest only in one [area of responsibility] to be mitigated globally in near real time. Likewise, while synchronizing CO missions related to achieving [combatant commander] objectives, some cyberspace capabilities that support this activity may need to be forward-deployed; used in multiple AORs simultaneously; or, for speed in time-critical situations, made available via reachback,” it states. “This might involve augmentation or deployment of cyberspace capabilities to forces already forward or require expeditionary CO by deployment of a fully equipped team of personnel and capabilities.”
—————
Free Secure Email – Transcom Sigma
Boost Inflight Internet
Transcom Hosting
Transcom Premium Domains