More than 95% of companies today use cloud services, and 83% store sensitive data in the cloud. Mobile devices and laptops allow for work to occur both inside and outside the network, pushing the boundary for security to a new edge defined by the cloud. Yet only 30% of companies today can protect data with the same policies on their devices, network, and in the cloud. Only 36% can enforce data loss prevention (DLP) rules in the cloud at all. And sixty percent currently have no way to stop a personal, unsecured mobile device from downloading sensitive data from the cloud, completely invisible to IT.
We’re in the midst of a transition from the network-centric, walled-garden model of security to one defined by device and cloud control points, which allows for freedom of motion to any location where work gets done, and in any cloud service.
We call this a Unified Cloud Edge. It is our vision for how companies can secure their data in a consistent manner as it moves between devices and the cloud, and from cloud to cloud. By following the data, we can see this vision come to life:
- Data at the device, going to the cloud. Data Loss Prevention (DLP) stops any data that should not enter the cloud from leaving a managed device.
- Device access to data in cloud services. The combination of a Cloud Access Security Broker (CASB) and Secure Web Gateway (SWG) control access to all cloud services, with the CASB controlling access to sanctioned services like Office 365 and the SWG covering every other service, including Shadow IT.
- Data in the cloud, moving from cloud to cloud. CASB uses an API-based connection to cloud services for complete visibility and control over data within the cloud services you sanction, as well as data in motion from one cloud service to another. And machine learning capabilities give you the ability to stop threats in the cloud.
- Data in the cloud, going to an unmanaged, personal device. CASB uses a reverse proxy to enforce authentication to your sanctioned cloud services, blocking access to any devices you don’t want to access your data, such as a personal iOS or Android devices.
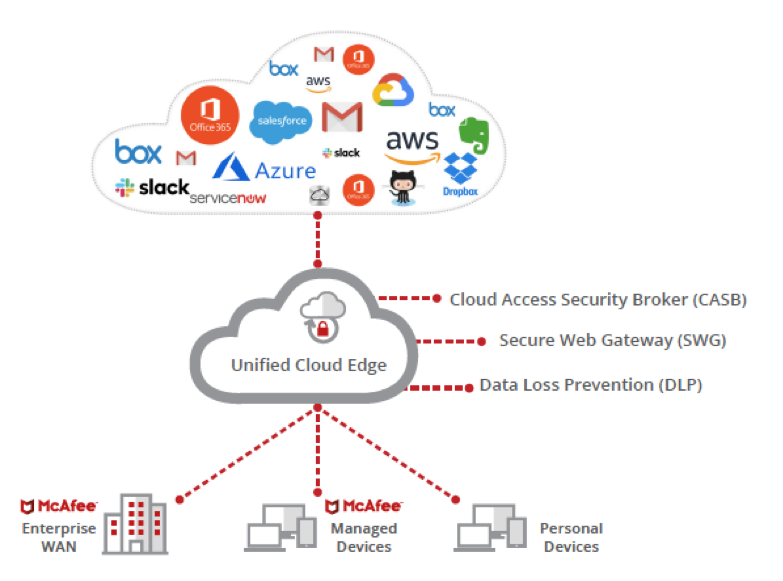
Figure 1: Simplified architecture for Unified Cloud Edge
Each of the control points in this architecture are built to work together seamlessly. In our Technical Preview of Unified Cloud Edge, we go into more detail on the management and policy creation experience, with examples of what you’ll see day to day. Head over here to download it.
For security and data protection admins, we know much of the daily work is allocated to investigation and incident management workflows. That’s why with Unified Cloud Edge, we’ve centralized all reporting, incident management, and investigation workflows for endpoint, network, and cloud data protection in McAfee ePO. For our customers with existing data protection classification and policies in ePO, we’ve also enabled a simple synchronization to our CASB for fast and efficient policy creation in the cloud.
Keep reading in our detailed Technical Preview of Unified Cloud Edge here, and contact us if you want to discuss implementation at your organization.
The post Security is Shifting to a Unified Cloud Edge appeared first on McAfee Blogs.
Premium Domain Names – transcom.uk
Transcom ISP – The UK’s Best Business ISP
DoubleCheck any website at doublecheck.uk